Last update images today Cyberspace Protection Condition Levels Chart






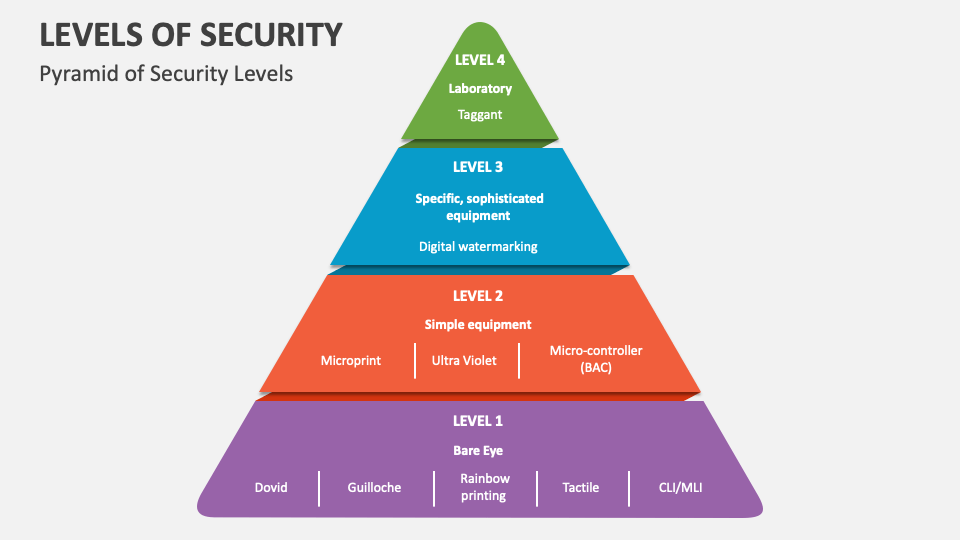







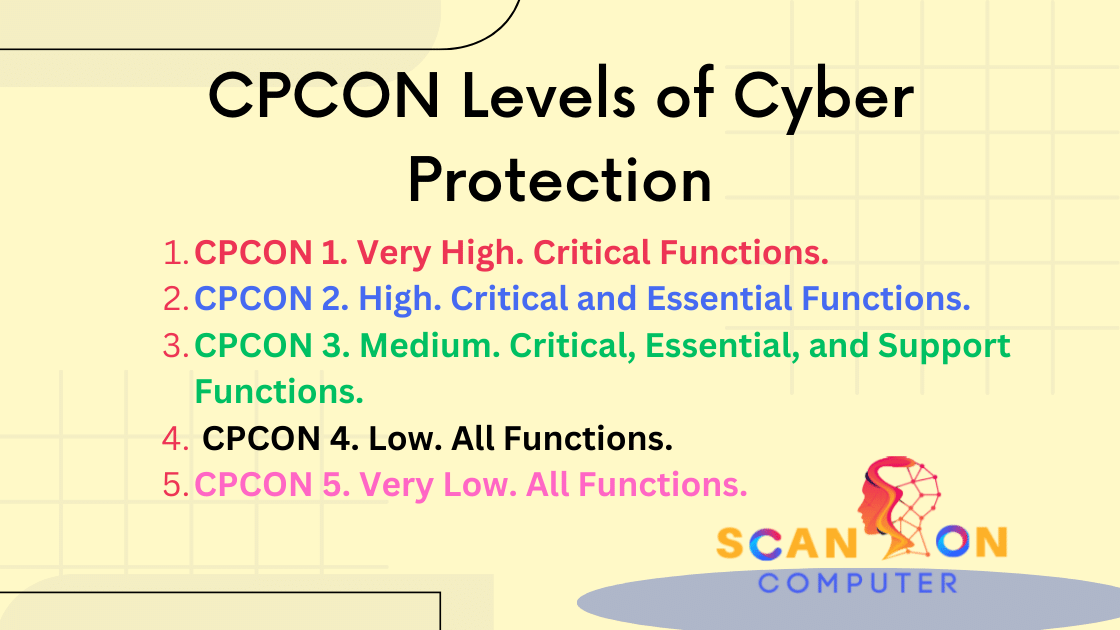





https www webitservices com wp content uploads 2022 08 img blog cybersecurity risk levels 2 jpg - 1 Top Cyber Risks 2024 Aida Loreen Img Blog Cybersecurity Risk Levels 2 https scanoncomputer com wp content uploads 2023 09 CPCON Levels of Cyber Protection png - 1 CPCON Levels Of Cyber Protection Scan On Computer CPCON Levels Of Cyber Protection
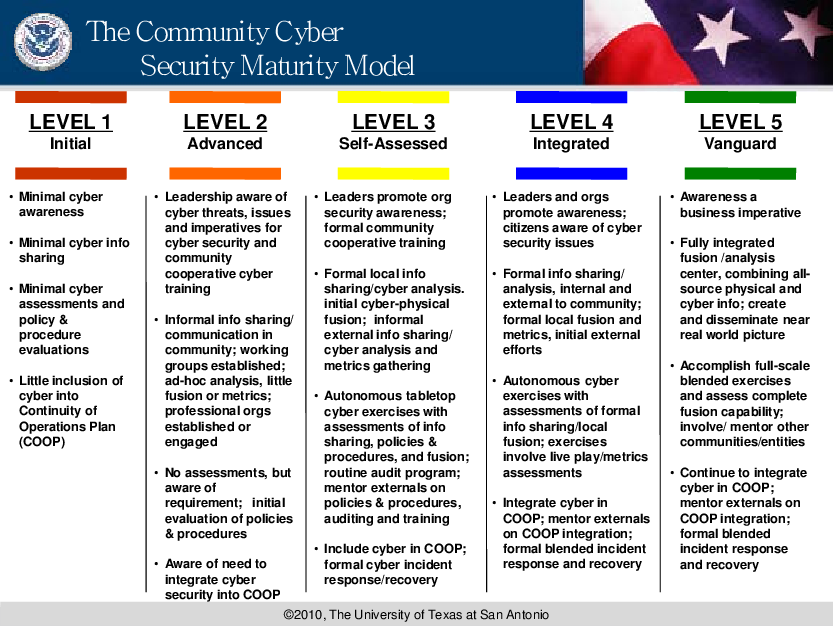
https i pinimg com originals aa 92 20 aa9220cc363c53142c320cb6a455ce77 jpg - 1 Pin De Nitlesh Naidu En Online Threats Seguridad Inform Tica Aa9220cc363c53142c320cb6a455ce77 http www riskmanagementmonitor com wp content uploads 2015 03 Screen Shot 2015 03 19 at 2 38 29 PM png - 1 Insider Threats Missing From Most Cybersecurity Plans Risk Management Screen Shot 2015 03 19 At 2.38.29 PM https www slideteam net media catalog product cache 1280x720 c y cyber threat security maturity model with protection levels slide01 jpg - 1 Cyber Threat Security Maturity Model With Protection Levels Cyber Threat Security Maturity Model With Protection Levels Slide01
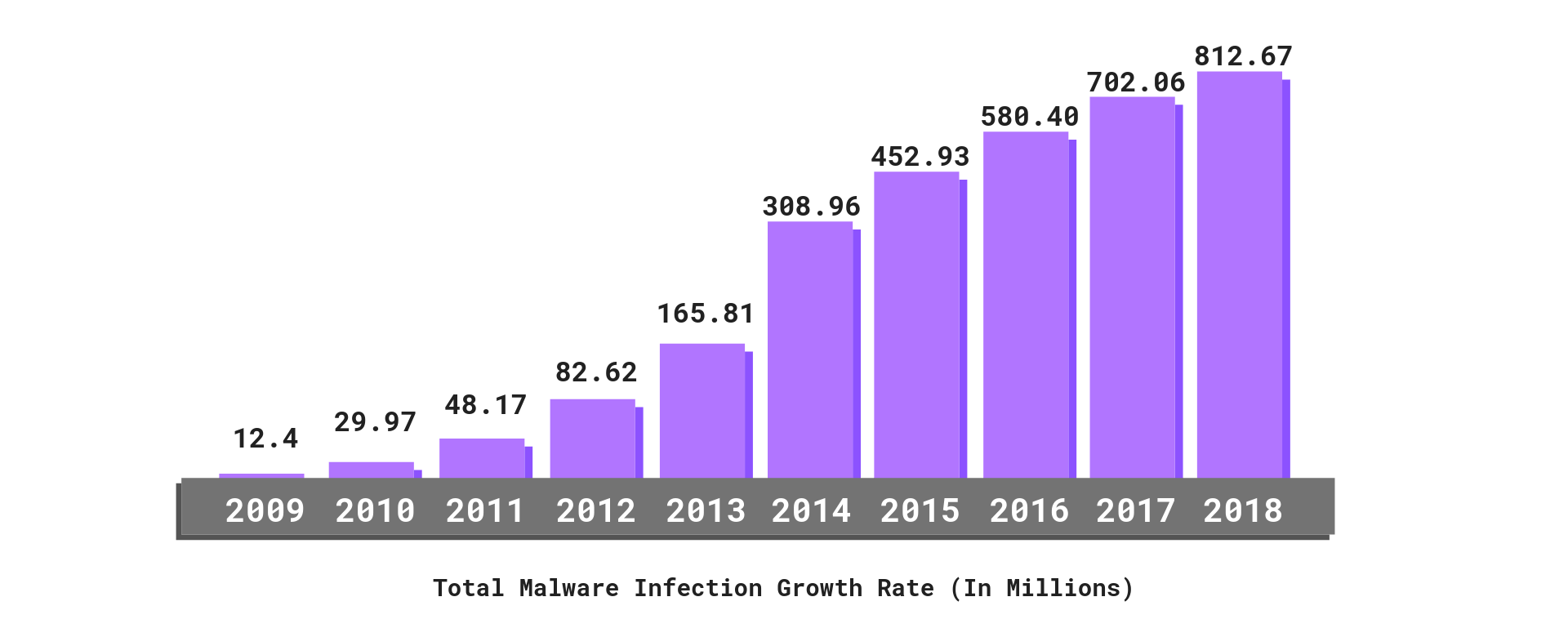
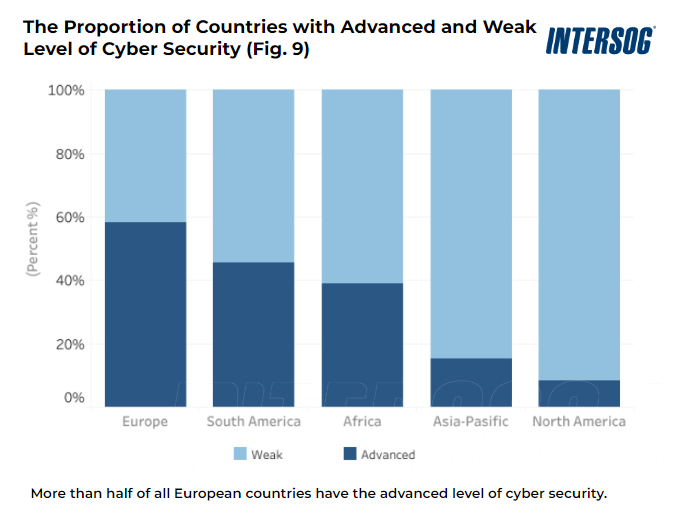
https intersog com wp content uploads 2022 11 advanced weak cybersecurity levels png - 1 Global View Of Cyber Security Advanced Weak Cybersecurity Levels https purplesec us wp content uploads 2019 03 Malware Infection Growth Rate Cyber Security Statistics png - 1 2023 Cyber Security Statistics The Ultimate List Of Stats Data Malware Infection Growth Rate Cyber Security Statistics
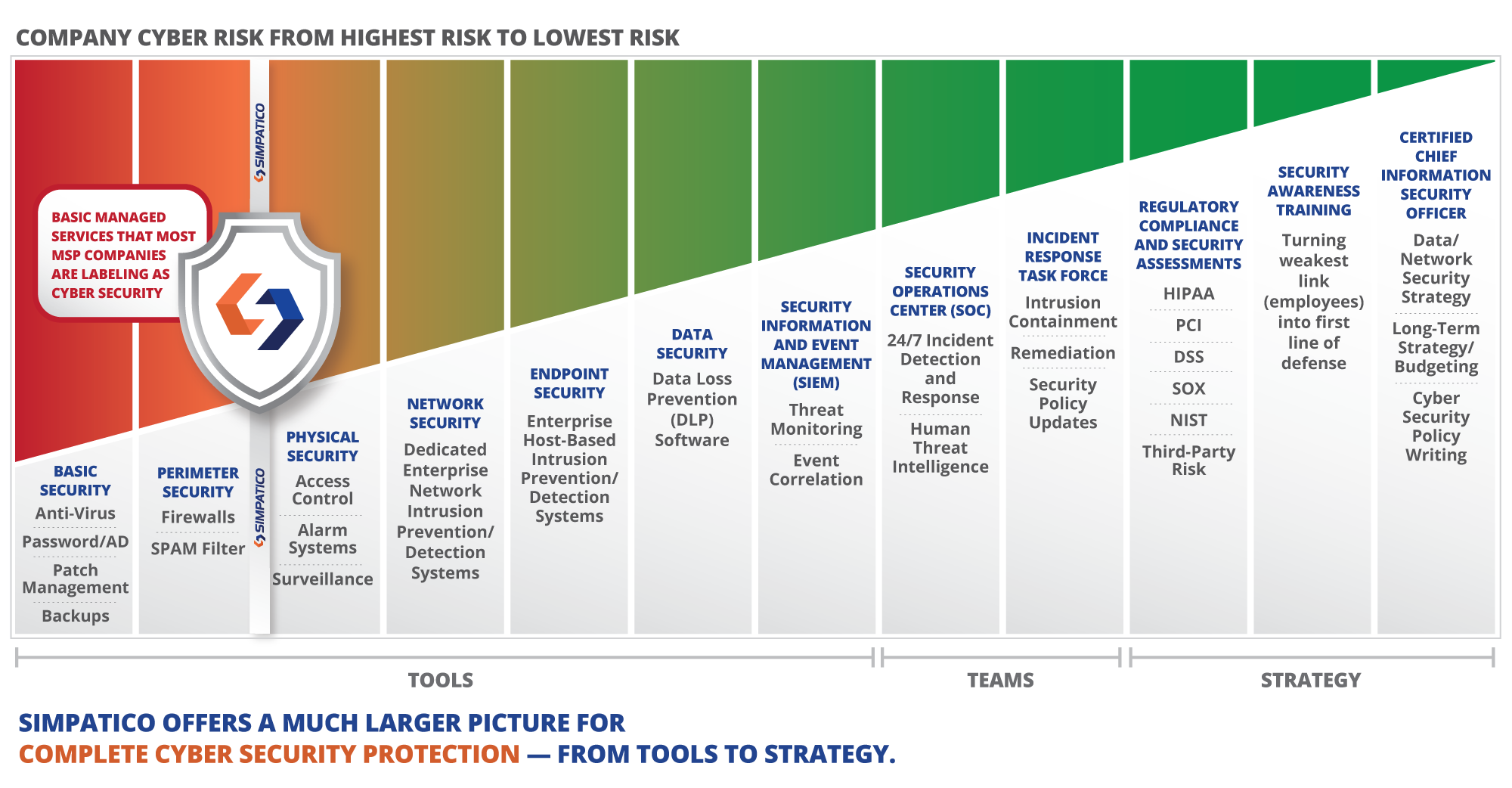
https www webitservices com wp content uploads 2022 08 img blog cybersecurity risk levels 3 jpg - 1 Cybersecurity Risk Levels Where Do You Draw The Line Naperville Img Blog Cybersecurity Risk Levels 3
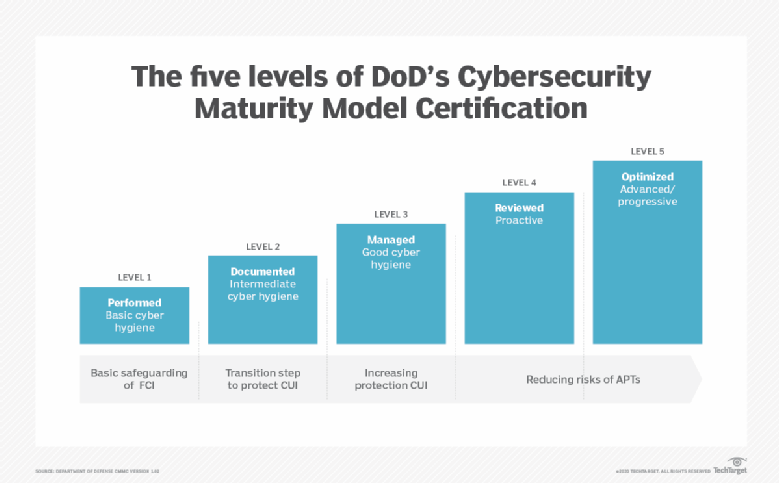
https www pumpsandsystems com sites default files 0315 CyberSecurityFigure1 colorTJ jpg - 1 How To Protect Plants From Invisible Threats Pumps Systems CyberSecurityFigure1 ColorTJ https cdn ttgtmedia com rms onlineImages security five levels of dod cybersecurity f desktop png - 1 Navigate The DOD S Cybersecurity Maturity Model Certification Security Five Levels Of Dod Cybersecurity F Desktop
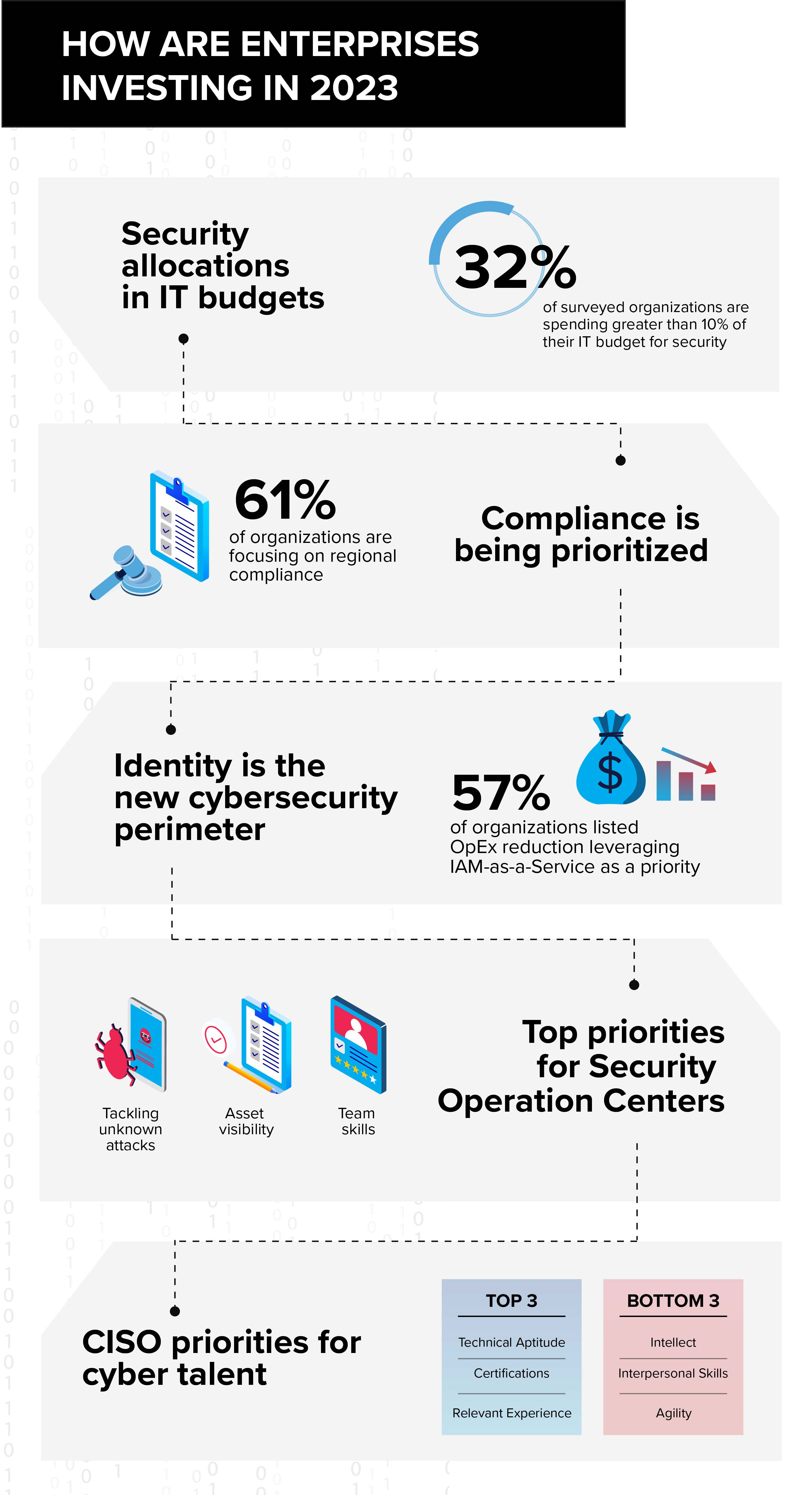
https www webitservices com wp content uploads 2022 08 img blog cybersecurity risk levels 2 jpg - 1 Top Cyber Risks 2024 Aida Loreen Img Blog Cybersecurity Risk Levels 2 https www insightsforprofessionals com getmedia 18e9699a bf3d 4ef6 a2ef 21ba05f9c3fb IFP Enterprise Security Article Images 1080px and 1600px v1 3 500 - 1 The Cybersecurity Threat Landscape In 2023 Research Insights IFP Enterprise Security Article Images 1080px And 1600px V1 3 500
https www pumpsandsystems com sites default files 0315 CyberSecurityFigure1 colorTJ jpg - 1 How To Protect Plants From Invisible Threats Pumps Systems CyberSecurityFigure1 ColorTJ https www researchgate net publication 274635658 figure fig2 AS 613964106956800 1523391858147 Five maturity levels of cyber security source WEF 7 png - 1 Cyber Security Maturity Model Levels Five Maturity Levels Of Cyber Security Source WEF 7 https purplesec us wp content uploads 2019 03 Malware Infection Growth Rate Cyber Security Statistics png - 1 2023 Cyber Security Statistics The Ultimate List Of Stats Data Malware Infection Growth Rate Cyber Security Statistics
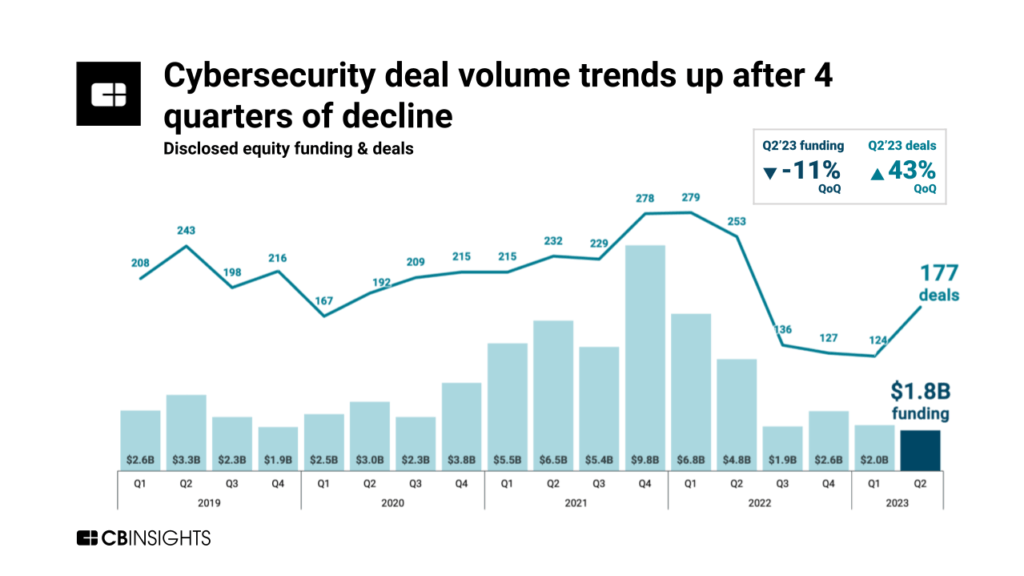
https research assets cbinsights com 2023 09 28133954 StateOfCybersecurityDealsFundingv2 1024x576 png - 1 The State Of Cybersecurity In 5 Charts CB Insights Research StateOfCybersecurityDealsFundingv2 1024x576 https blog auditanalytics com wp content uploads 2020 05 Blog Graphic Cybersecurity Report 2020 Number of Breaches png - 1 Trends In Cybersecurity Breach Disclosures Trends In Cybersecurity Blog Graphic Cybersecurity Report 2020 Number Of Breaches
https www webitservices com wp content uploads 2022 08 img blog cybersecurity risk levels 3 jpg - 1 Cybersecurity Risk Levels Where Do You Draw The Line Naperville Img Blog Cybersecurity Risk Levels 3
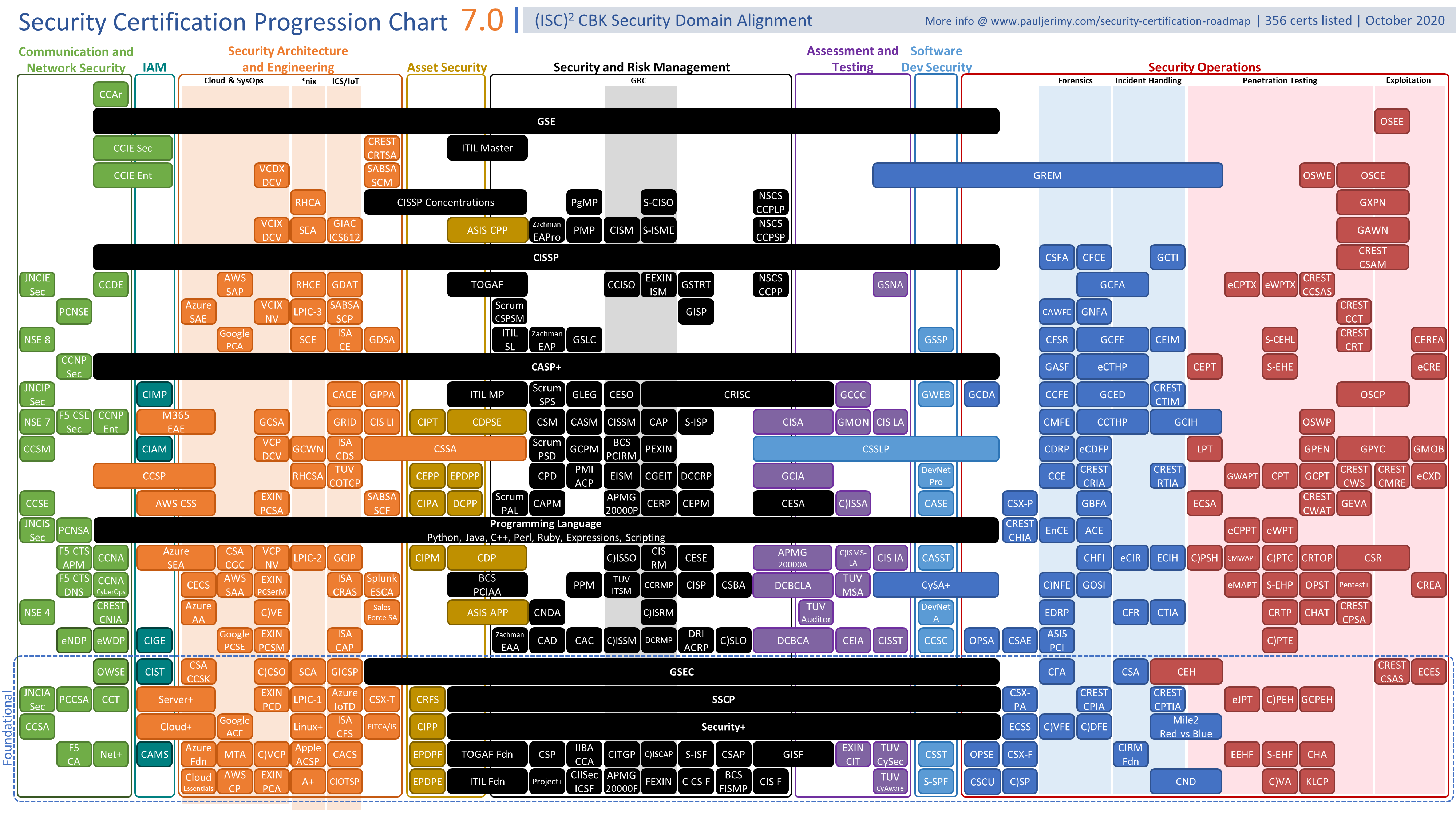
https edrawcloudpublicus s3 amazonaws com edrawimage work 2022 12 7 1670384778 main png - 1 Cyber Security Diagram EdrawMax Template Main https i pinimg com originals aa 92 20 aa9220cc363c53142c320cb6a455ce77 jpg - 1 Pin De Nitlesh Naidu En Online Threats Seguridad Inform Tica Aa9220cc363c53142c320cb6a455ce77
https p16 ehi va gauthmath com tos maliva i ejcjvp0zxf us 375bed0813954ddb85ff99d7e1073152 tplv ejcjvp0zxf 10 image - 1 Solved Under Which Cyberspace Protection Condition CP CON Is The 375bed0813954ddb85ff99d7e1073152~tplv Ejcjvp0zxf 10.imagehttps www slideteam net media catalog product cache 1280x720 c y cyber threat security maturity model with protection levels slide01 jpg - 1 Cyber Threat Security Maturity Model With Protection Levels Cyber Threat Security Maturity Model With Protection Levels Slide01
https purplesec us wp content uploads 2019 03 Malware Infection Growth Rate Cyber Security Statistics png - 1 2023 Cyber Security Statistics The Ultimate List Of Stats Data Malware Infection Growth Rate Cyber Security Statistics https research assets cbinsights com 2023 09 28133954 StateOfCybersecurityDealsFundingv2 1024x576 png - 1 The State Of Cybersecurity In 5 Charts CB Insights Research StateOfCybersecurityDealsFundingv2 1024x576 https i pinimg com originals aa 92 20 aa9220cc363c53142c320cb6a455ce77 jpg - 1 Pin De Nitlesh Naidu En Online Threats Seguridad Inform Tica Aa9220cc363c53142c320cb6a455ce77
https i pinimg com 736x 04 7b 40 047b40f87e9614fc78b044b846921d5e jpg - 1 Image Result For Cybersecurity Incident Response Plan How To Plan 047b40f87e9614fc78b044b846921d5e https www insightsforprofessionals com getmedia 18e9699a bf3d 4ef6 a2ef 21ba05f9c3fb IFP Enterprise Security Article Images 1080px and 1600px v1 3 500 - 1 The Cybersecurity Threat Landscape In 2023 Research Insights IFP Enterprise Security Article Images 1080px And 1600px V1 3 500
https blog auditanalytics com wp content uploads 2020 05 Blog Graphic Cybersecurity Report 2020 Number of Breaches png - 1 Trends In Cybersecurity Breach Disclosures Trends In Cybersecurity Blog Graphic Cybersecurity Report 2020 Number Of Breaches